Mark of the Web: A Defender’s Ally or an Attacker’s Obstacle?
In this blog post, our security research team dives into the details of Mark of the Web (MoTW) feature on Windows and the recent 7-Zip bypass.

Introduction
Have you ever attempted to open a file downloaded from the internet, only to be met with security warnings alerting you that the file is unsafe? This is where Mark of the Web (MotW) comes into play, where it can be used by Microsoft Defender SmartScreen to protect users from potentially unsafe content originating from untrusted sources. This blog delves into Mark of the Web (MotW), explaining its purpose, its impact on security, and how applications enforce it to mitigate risks. Mark of the Web (MotW) is a form of Alternate Data Streams (ADS) in Windows that specifies information about downloaded files, enabling further inspection of the downloaded objects through the Microsoft Defender SmartScreen. Before diving into the MotW, it is essential to understand several key concepts to fully grasp its role in Windows security.
Alternate Data Streams (ADS)
ADS are forms of metadata used in Windows that allow more than one ‘data stream’ to exist in a file (or directory), essentially called Alternate Data Streams. It was historically created for compatibility with the Macintosh file system. The default ADS in Windows is called $DATA, which is typically associated with files and directories that contain one or more data streams. ADS is a feature of NTFS, the default file system of Windows. Unlike traditional metadata, ADS can store any form of data, independent of the original file's format. This allows ADS to hold additional information, such as metadata, scripts, or even entire executable content, without altering the primary file’s size or structure. ADS can be associated with files and directories through the format <file/dir_name>:<stream_name>. As an example, a normal text file called file.txt can have another data stream called calc (in addition to its original default data stream$DATA) . This data stream can be viewed using the format file.txt:calc. ADS are usually hidden from the user and cannot be easily interacted with. Moreover, ADS are not considered as content inside a file, rather, they are considered part of the file's metadata. They do not affect the file's integrity nor are they calculated with the file's size. However, they are calculated in the overall disk space. Finally, since ADS are a feature of NTFS, transferring files with ADS from NTFS systems to non-NTFS systems will remove the MotW, since it is not supported on non-NTFS systems.
Interacting with ADS
In general, we can read, write to, and execute ADS. There are various ways to interact with ADS, one of which is through the following PowerShell Cmdlets, which are very familiar and common:
Add-ContentClear-ContentGet-ContentGet-ItemRemove-ItemSet-Content
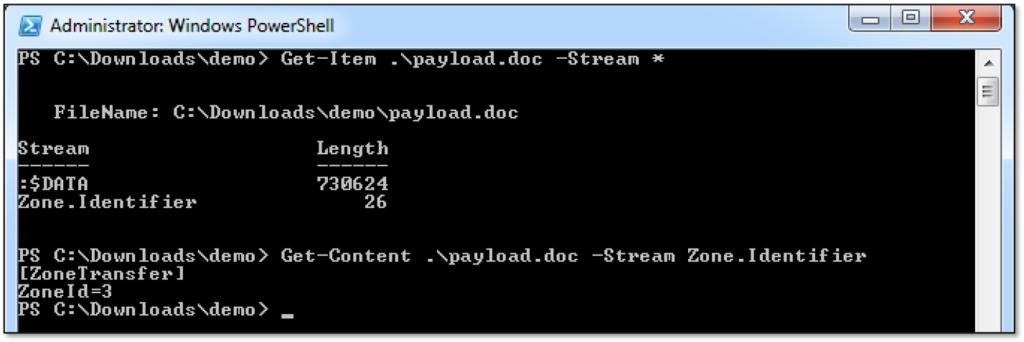
For this blog, we are going to demonstrate how to read streams. However, ADS can be used to conduct malicious actions and execute malicious files from within the streams using special techniques that we could discuss in the future. To list the streams of a file or files in a directory, or the directory itself:
Get-Item -Path * -Stream *
Get-Item -Path <file/dir_path> -Stream <stream_name>To read/view the content of a stream associated with a file or directory:
Get-Content -Path <file/dir_path> -Stream <stream_name>Microsoft Defender SmartScreen
Microsoft Defender SmartScreen is a cloud-based security feature integrated into Windows, Microsoft Edge, and - previously - Outlook to protect users from malicious websites, phishing attempts, and the dangers of downloaded content. It consists of several key components that operate across different areas of the Windows ecosystem:
- Microsoft Edge SmartScreen – Analyzes URLs and webpage behavior to block phishing sites, deceptive downloads, and malicious web content using a cloud-based reputation system.
- Windows OS-Level SmartScreen – Evaluate downloaded files and executables, using reputation-based analysis and Mark of the Web (MotW) to warn users about potentially harmful programs before execution.
- Microsoft Defender for Office 365 (Replaces Outlook SmartScreen) – Scans emails, attachments, and links to detect phishing, malware, and fraud attempts.
Together, these components enhance Windows security by proactively detecting and mitigating threats across different attack vectors. Now that we have covered the necessary background, we are ready to introduce the MotW.
Mark of the Web (MotW)
MotW is essentially an ADS (usually named Zone.Identifier) that gets automatically written by browsers on downloaded objects, either by directly writing an ADS to the object or by using the system's IAttachmentExecute interface (shobjidl_core.h) to accomplish this task. The MotW is used to indicate that this object was downloaded from the internet and has a potential associated risk with it. Microsoft Defender SmartScreen uses this information to assess downloaded files and warn the user before execution, helping prevent the execution of potentially malicious programs.
It is worth noting that downloading files using command line utilities (i.e. Cmd and PowerShell) will not add MotW, because it is added by supporting browsers or any application that enforces it.
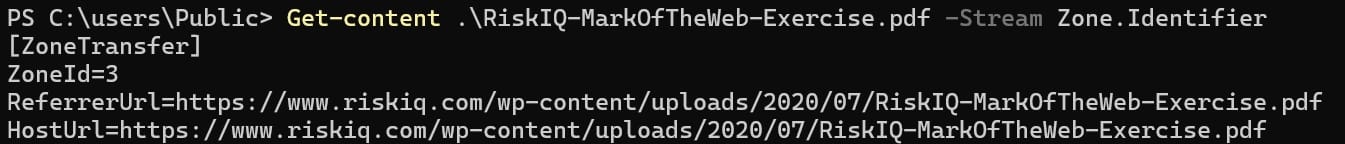
In the Zone.Identifier stream (MotW) associated with downloaded files, we usually find the following entries:
- ZoneId: [A number between 0-4]
- ReferrerUrl: The website that this file/program came from
- HostUrl: The exact link where we got this file
The ZoneId can have the following values, indicating the source of the downloaded file:
0 - Local computer
1 - Local intranet
2 - Trusted sites
3 - Internet
4 - Restricted sites
As an example, if we download the following PDF from the browser and read the Zone.Identifier stream (MotW), we will find the following information:
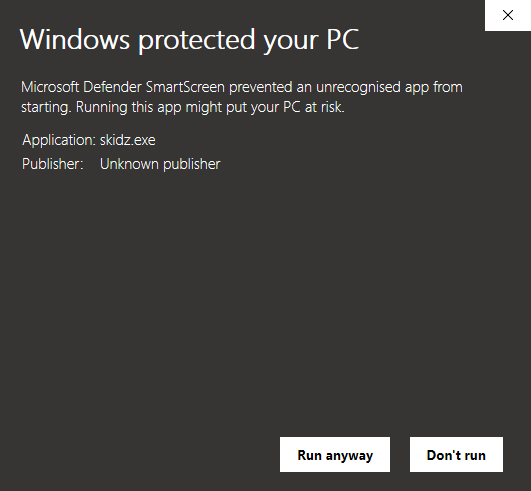
Through MotW, SmartScreen identifies the source of the downloaded content, and in addition to the content itself, it checks them with lists of known malicious websites and programs and other lists of well known files and programs that are downloaded frequently. The following is an example of a SmartScreen warning upon running a potentially unsafe downloaded executable skidz.exe.
Another type of prompt that is indirectly associated with MotW that a user might see is the following prompt that appears to warn users when interacting with files with high-risk extensions.

To summarize, MotW can be thought of as an additional barrier to phishing attempts where it grants the user the ability to deny execution.
How to bypass MotW?
Now that we know what MotW is and how it is set and used as a protection line, we can discuss how we would bypass it:
- Since MotW is an ADS, and ADS is a feature of NTFS, we can conclude that file formats that do not support NTFS, such as container file formats (i.e. .vhd, .vhdx, .iso, .img, etc) will essentially bypass this whole additional protection provided by MotW since they will not be able to propagate the MotW to their embedded content. It is worth noting that the container file may have a MotW itself, but any payload/content inside of it will not.
- Another path that we could take is to abuse applications that do not add or propagate the MotW. An example of such an application is the 7z software, that recently started supporting Windows MotW. In addition to 7z, the Git client also does not add MotW to files downloaded using it, and it makes sense sometimes to do so. Imagine downloading a whole repository and having to assign MotW to each and every file.
CVE-2025-0411
In this advisory CVE, it was found that double compressing a payload using 7z compression then delivering it to the victim and having the victim execute the original file within the double compression removes the MotW, resulting in bypassing the protections introduced by it.
Conclusion
MotW can be an interesting component from multiple perspectives. Red Teamers are interested in bypassing techniques, usually increasing their phishing success rates while Blue Teamers tend to find more accurate detection for such activities and bypassing attempts.
Also, we can deduce that MotW is one of the barriers that significantly contributed to the decline of macro-based attacks. All Office applications block macros downloaded from the internet.
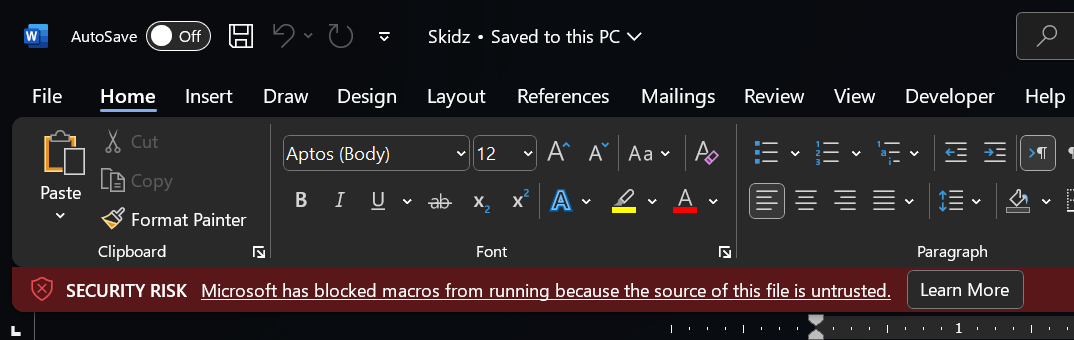
SmartScreen isn't the only component that makes use of the MotW, other programs may also use it to warn users of potential impacts of downloaded files. For instance, SmartScreen displays warning prompts for downloaded files, while Microsoft Office uses MotW to trigger security measures, such as opening files in a sandboxed environment or blocking macros if detected. Similarly, Visual Studio presents warning messages when opening files obtained from the internet. These protections all rely on the presence of the MotW stream to enhance security.
References